TORONTO—As is customary, this year’s Hospitality Industry Technology Exposition & Conference began with a session on cybersecurity and best practices for data protection. Unlike previous years, which focused on the trends and mentality behind hackers and why they target hotels, this session was all about offense.
Beginning with physical security, the panelists asked those in attendance if their company is prepared for a potential security breach—an event many consider to be inevitable. Jeremy Rock, owner of the Rock IT Group, said hotel operators should restrict access to their internal systems to employees who actually need it, and no one else.
“We’ve investigated [property-management systems] around the world, and the number of people who have access to credit card information is astounding,” Rock said. “Housekeeping employees, people in engineering; is that necessary? Also, people join and leave your teams all the time, so make sure you are on top of that and take old employees off your system.”
It’s a lesson some hotels have learned the hard way, as just one moment of action from a disgruntled employee can cause tens of thousands of dollars in damage in a short period of time. Rock also said to install and maintain a working firewall for security using a formal approval and testing process for all external network connections.
Above all, Rock said hotels need to disallow any direct routes of traffic from forming, inbound or outbound, between the internet and your hotel’s cardholder data environment. He recommended creating what he referred to as a “DMZ” (demilitarized zone) to limit inbound and outbound traffic to only the most crucial protocols necessary for the cardholder data environment.
“Also, operators should be encrypting cardholder data, and you can’t have any personal account info being transferred through email ever,” Rock said.
Rock also said hoteliers, and businesses in general, tend to have slack attitudes toward antivirus protection and updates. This can no longer be allowed. “People fall behind on updates or don’t allow them,” he said. “When patches come out they sometimes tend to be problematic, so I understand not installing them right away, but don’t let them go uninstalled for too long. One month is long enough to wait, and this is a policy that should be adhered to.”

Credit or ID?
This sort of strict policing is necessary in today’s world as data breaches become more common—and more thorough. Daniel Johnson, partner and co-founder of Venza, said hoteliers need to realize the consequences of data breaches beyond compensation due to bank fines, audits and remediation costs.
“Personal information is more valuable these days than credit card data, and results in a larger loss in consumer confidence if it is stolen,” Johnson said. “In North America, most people can get their money back if their credit card data is stolen. If that data goes missing, a guest’s view of a property may fall but the impact in reputation will be manageable. But if their personal identity is stolen during their stay, that leaves a larger, more far-reaching impact on satisfaction.”
The traditional target for these kinds of attacks is the property-management system because it is historically the “bank” for credit card transaction data. But Johnson said the growing fascination with the Internet of Things in hospitality leaves emerging technology open to vulnerabilities because hackers whittle away at the path of least resistance.
“Too many operators want to know what the minimum requirements are for security, and often that is [payment card industry] compliance,” Johnson said. “So many of them take out the fluff, going right to PCI compliance to check that box and put their people back on the floor. [Data] security isn’t something you can throw into place and hope for the best.”
Rock said documentation is going to become much more important in the near future as the industry increasingly invests in mobile devices and applications. He also observed that many operators allow staff to access hotel networks on personal devices, and hoped somewhat forebodingly that none of these personal devices had access to the hotel’s point-of-sale system. Furthermore, he said too many operators are unaware of who actually owns the network their property is running on, which can create chaos in the event of a breach.
“Often you have a hotel, an owner, a wireless network provider, a brand dictating things, a management company, an outsourced IT support company or outsourced [audiovisual] operator, and in many cases a combination of them are at play,” Rock said. “Knowing who manages all of these for you and who is interacting with all your firewalls is key.”
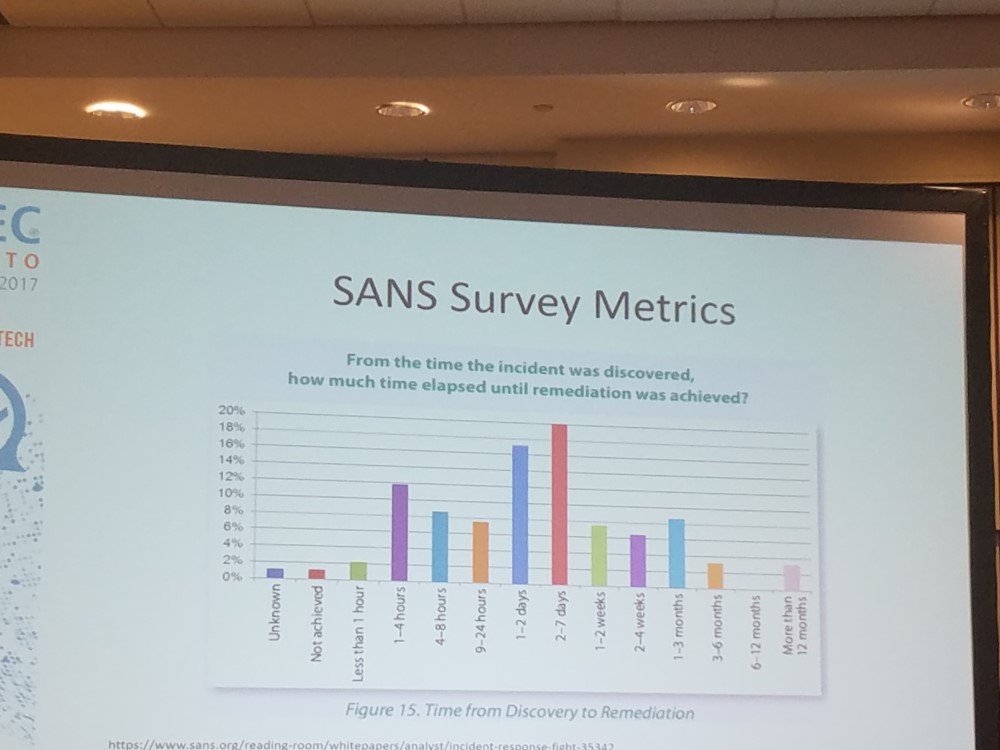
Plan for the worst
If Rock had his way, he would suggest hotels prioritize online transactions to ensure no data is stored on a physical device at any time. But should an incident occur, what are your options? Hiranya Maru, director of information security at Marriott International, said it is necessary to create an incident response plan to assist you in your decision making. Everything from denial of service attacks to loss of equipment, unauthorized access to private equipment or locating a card skimmer installed on a POS all qualify as “incidents” tailored for these reports, which focus on preparation, detection and analysis.
“Is law enforcement going to protect [your property]? Yes, but how do you get ahead of it, or communicate about an incident with guests or staff? That’s why you need a plan to contain or respond to a threat that may occur,” Maru said. “Create a team structure to lead and respond to the incident, someone to communicate with media, someone to call law enforcement, the bank or PCI vendors and so on.”
Maru said the actions taken by a hotel after an incident occurs are time sensitive when it comes to preventing further damage from occurring. Taking immediate action is necessary, even if it begins with changing all passwords on property.
“Incidents will happen whether you have a plan for them or not,” Maru said. “Lacking a plan leads to lost or stolen guest data. Preparation won’t prevent incidents from happening, but it will keep you ahead of them.”
